

In the modern workplace, digital security threats are a never-ending concern and it needs immediate attention as these data thefts not only removes data from the owner but create an additional unauthorized copy. Security barriers are now set high to protect the company assets from hackers and careless admins.
Multi-Factor Authentication is a method that provides an enhanced level of security to business environments by eliminating issues around identity thefts and protects digital assets.MFA is one of the most effective security controls for protection of on-premise and cloud data. MFA also contributes to enabling enterprise mobility as users get the flexibility and on-demand access to the applications and devices they wish to, without compromising on network and data security.

CloudAuth Multi-factor Authentication is specially built for enterprises to easily set up multi-factor authentication in one-click, for any infrastructure with minimal administrative overhead. SecureKloud addresses the solid challenges in MFA adoption by progressive asset addition, large number of authentication factors where enterprises can choose the authentication factors based on the asset criticality and need, and finally getting this done without incurring costs of hosting, equipment, and personnel: especially when the number of critical assets increases day-by-day. SecureKloud’s Multi-Factor Authentication facilitates a quick and easy set up of MFA for an enterprise without deploying new software in your local network or distributing new hardware to employees.
CloudAuth MFA is robust and scalable enterprise security platform that can authenticate huge number of unique identities in seconds.
Almost 81% of cyber-attacks are attributed to weak passwords. It just takes less than 10 minutes to crack an 8-character password. These security/ data breaches cause loss of data and opportunity for enterprises that can cost around $3500/ employee/ breach. Hence, in this digital era, it is imperative that critical assets are protected and there is zero tolerance on breach.
CloudAuth MFA uses novelencryption techniques during data transfers between CloudAuth server and client module, It secures variety of enterprise applications – 500+ federated SaaS applications, internal and external federated applications, VPN services, AWS Services etc., including integration with AD and LDAP.CloudAuth supports FIDO2, U2F based possession factors and AI/ML based biometric factors to provide a simple and fast authentication experience.
CloudAuth MFA is a powerful platform that accelerates MFA adoption, ensuring highly secured access todigital assets without compromising on the user experience in simple steps,
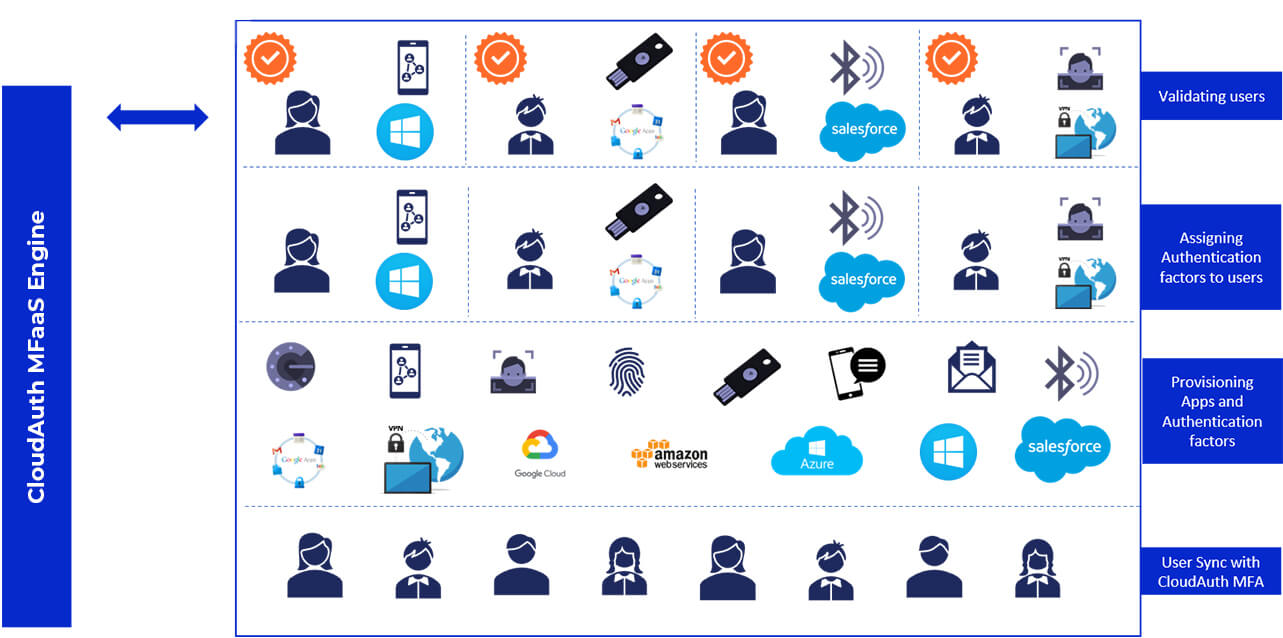
Authentication factors are the different methods through which a user authenticates his/her identity. MFA enables enterprises to have one or more authentication factors such as knowledge factor, possession factor, Inherence factor in various combinations based on enterprises' requirements. The availability of multiple authentication factors and the flexibility to opt for the required combination of authentication factors is what sets CloudAuth apart.
CloudAuth MFA is an intuitive platform with a comprehensive portfolio of authentication factors along with prebuilt SaaS app integrations. CloudAuth Adaptive MFA authenticates users based on contextual & behavioral factors. We offer flexibility to organizations to opt from a variety of factors including SMS/Email OTP, Mobile based Fingerprint Authentication, Face Recognition, Mobile Tap and third-party solutions like Hardware tokens (YubiKey), Google Authenticator, etc. Based on the risk associated with applications and the environment, enterprises can adopt the necessary factors for their enhanced security.

CloudAuth Adaptive MFA powdered by Artificial Intelligence (AI/ML) analyzes and understands the contextual behaviors such as location, device, login time and user behavior to perform the necessary security action during access authorization. It is a secure and flexible form of authentication that enables validating multiple factors to determine the authenticity of a login. These contextual factors used for validationminimizes the risk associated with aparticular user sign in. Therefore, authentication is allowed based on the following –

Among MFAs the most essential factor is an android & IOS based push notification app that Verifies users with a tap from their mobile device, to access various enterprise applications.
Despite how fast the business units want to move, there remains a need to adhere to rules and regulations. These might be HIPAA rules, SOX, Data Protection, etc. If an organization wants to entice over 10 million Facebook fans to come register on their site, they need to protect their identities. This diverse and dynamic user base creates challenges such as a multitude of devices being used to access an application (e.g. smartphones, tablets) and the regulatory environment promises to keep getting more complex, not simpler.
© 2021, SecureKloud Technologies. All Rights Reserved.